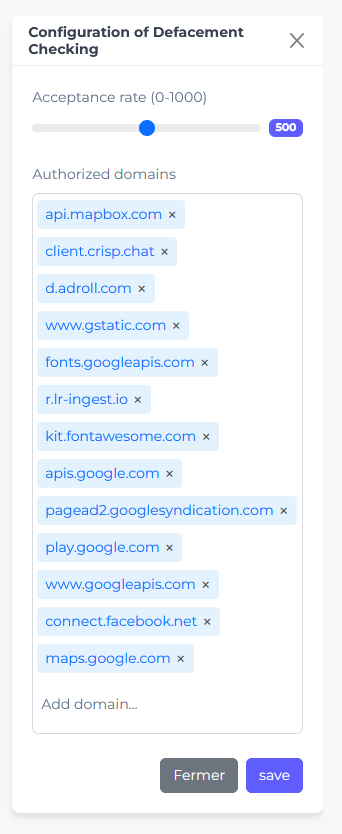
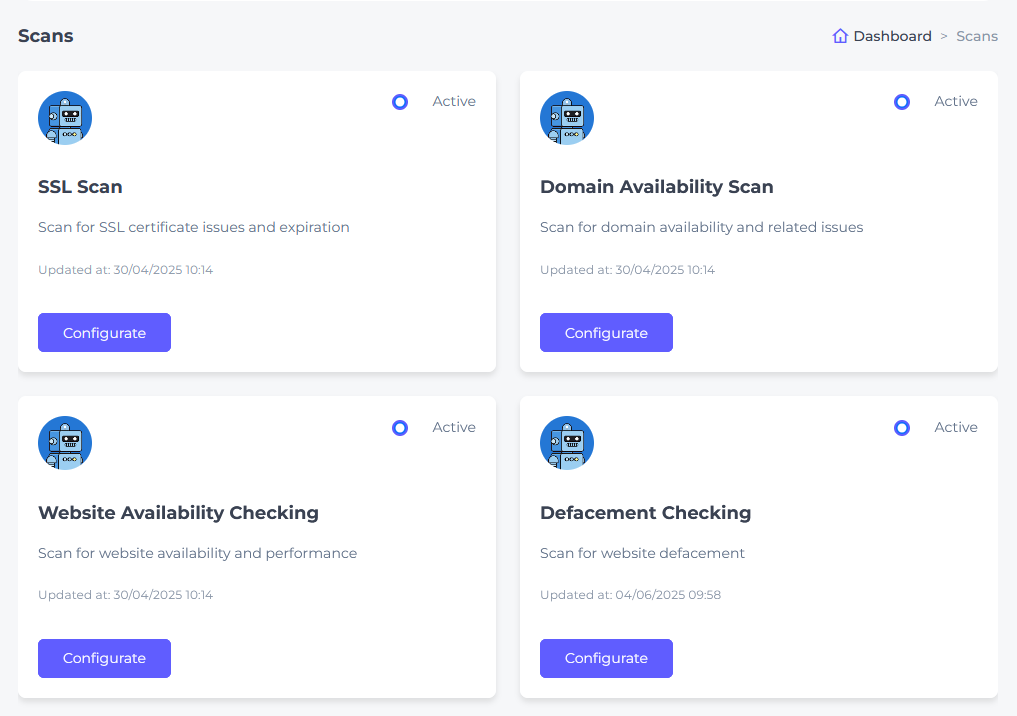
Scan Management
Overview
Scan Management controls Oju’s automated monitoring capabilities. Configure scan types, adjust detection criteria, and manage monitoring frequencies to ensure comprehensive security coverage for your entities and platforms.
Available Scan Types
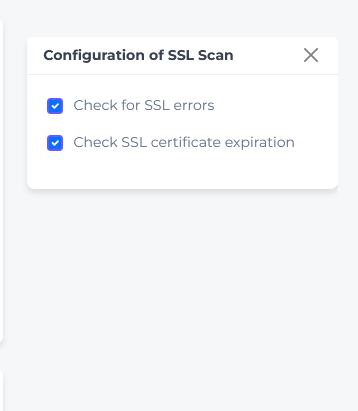
SSL Certificate Monitoring
Purpose: Monitor SSL certificate and validity
Configuration Options:
-
SSL Error Checking - Enable/disable SSL validation
-
Expiry Monitoring - Toggle expiration warnings
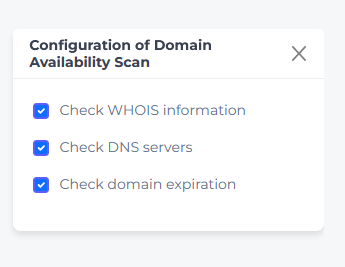
Domain Availability Scanning
Purpose: Monitor domain registration and DNS resolution
Configuration Options:
-
WHOIS Checking - Enable WHOIS for domain registration monitoring
-
DNS Server Validation - Test with configured DNS servers
-
Expiry Alerts - Monitor domain renewal dates
Monitoring Automation
Scan Scheduling
Automatic Execution:
-
Scans run based on configured frequency
-
System manages scan distribution
-
Celery task queue handles execution
Frequency Control:
-
Configured in system settings
-
Applies to all active scan types
-
Adjustable based on requirements
Scan Coordination
System Integration:
-
Scans coordinate with platform status
-
Only active platforms included
-
Results feed alert generation system
Resource Management:
-
Worker limits prevent overload
-
Proxy rotation for external checks
-
Cache management for efficiency
Effective scan management ensures comprehensive monitoring coverage while maintaining system performance and reliability.